- Static filter
Static vs Dynamic Filtering
Static (constant and unchanging) packet filtering offers security against novice hackers. You can configure the filtering rules when you install a firewall to filter based on source/destination IP addresses. This sets up a static filter. But static packet filtering does not have the intelligence to selectively open and close ports; it can either open all the non-private ports or close them all. If all ports are kept open, an intruder can break in; if all ports are closed, the firewall becomes obtrusive to the users on the network. (To see why ports are opened, see the section on FTP Security, below.)
- Dynamic filter
A dynamic firewall, in very basic terms, adapts to traffic by learning which ports are needed for a session, and closes all others. When a legitimate session is initiated, the firewall monitors the requests to open ports between the terminating points and opens only those. When the session ends, the firewall immediately closes the ports. No security holes are left on the firewall for hackers to enter. The Ascend Secure Access Firewall is a dynamic firewall that performs highly sophisticated filtering algorithms and detects even the most obscure methods of unauthorized entry.
FTP Security
Many companies recognize the commercial and partnering opportunities inherent in maintaining an FTP server, but are concerned about allowing inbound FTP sessions on their networks.
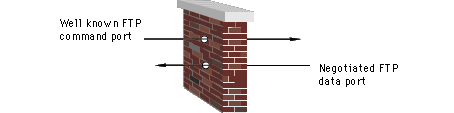
Routers, through packet filtering rules, can control external access of a network's FTP server by blocking many of the server's ports. A port is a numbered access point for data to enter and exit, not a physical connection. Each side of an FTP connection must know the other's port number to successfully send and receive data or commands. Port numbers below 1024 are generally reserved, or in the case of a network server, provide access to non-public applications and services. Ports between 1024 and 65535 are not considered private, and are available for other sessions. Therefore, each side of an FTP connection has nearly 65,000 possible TCP ports available.
During an FTP session, a router's packet filter can be a security risk because FTP requires two connections. One connection controls the session (does the negotiating and starts and stops the session); another connection supplies the conduit (port) through which data is transferred. By convention, the controlling connection uses well-known port 21 for FTP, and the router's filtering rules allow access to that established port number. Creating the data transfer connection exposes the security risk.
At the TCP level, the machines negotiate the port numbers which are used for the data connection. At the end of the these negotiations the ports are activated by the machines, but the router does not know the server's data connection port number because it is not part of the negotiations. Here is the security risk--the router does not know which of the server's thousands of ports will be chosen for the data connection, therefore it cannot block ports not required for the connection. This provides ample choices for probing attacks from unauthorized sources.
Static filtering cannot address this problem, but dynamic filtering monitors all packet headers. Very simply stated, the first packet (and every subsequent packet) contains the data connection's port address. If the rules you set up in the firewall allow the transaction to proceed through the negotiated port, the transfer is authorized and continues. But the firewall closes all other ports. When the session ends, the firewall immediately closes all ports. No security holes are left on the firewall for hackers or unauthorized users to enter.